The discovery about autofill functionality in Android-based apps accidentally leaking login credentials to the apps hosting the webpages will be presented at BlackHat Europe 2023, one of the most prestigious events for Information Security.
Password managers long touted as the holy grail of online security have come under scrutiny, thanks to the efforts of IIITH Prof. Ankit Gangwal and his MTech students Shubham Singh and Abhijeet Srivastava. In their paper “AutoSpill: Credential Leakage from Mobile Password Managers,” that won the Best Paper Award at the ACM Conference on Data And Application Security and Privacy (CODASPY) 2023, the researchers have revealed how login credentials can be inadvertently leaked by the Autofill functionality of mobile Password Managers.
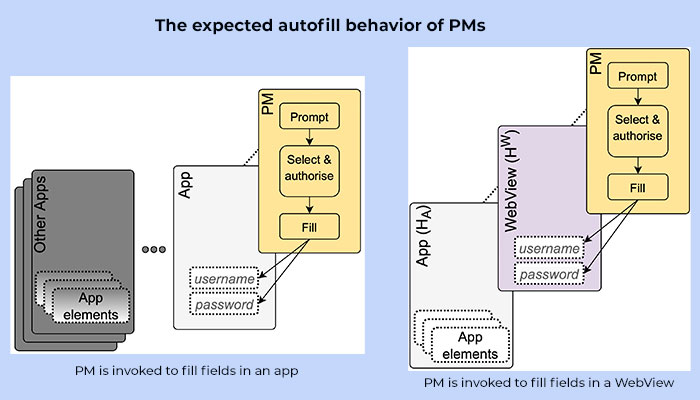
Cybersecurity experts have regularly advocated the usage of password managers for not only creating long and complex passwords but also helping you remember these credentials the next time you log in. With around 92.3% of internet users accessing the internet via a mobile device, it’s little wonder that Password Managers (PMs) have become more popular on these small screen devices due to the convenience of automatically filling in the required data on login forms. However, PMs on modern mobile operating systems work in a way that is fundamentally different from that on computers. When you are trying to log into an app on an Android Operating System (OS), the OS itself generates an auto filling request to the PM acting as an intermediary between the apps.
When AutoFill Becomes AutoSpill
It was while experimenting with the Autofill functionality of PMs on mobile OSes that Prof. Gangwal from the Centre for Security, Theory and Algorithmic Research (CSTAR) and his team discovered; what they term as an AutoSpill attack. They found that every time an app loads a login page in WebView, and an autofill request is generated from that WebView, the PMs and the mobile OS get disoriented about the target page for filling in the login credentials. While the expected behaviour is to populate the login page in WebView, the app loading the WebView could get access to the sensitive information. Prof. Gangwal explains with the help of an example, “Let’s say you are trying to log into your favourite music app (eg. Spotify) on your mobile device, and you use the option of “login via Google or Facebook,” the music app will open Google or Facebook login page inside itself (i.e., within the music app) via the WebView. When the PM is invoked to autofill the credentials, ideally it should autofill only into the Google or Facebook page that has been loaded. But we found that the autofill operation could accidentally expose the credentials to the base app, which in this case is your music app.” The ramifications in a scenario where the base app is a malicious one are humongous. “Even without phishing, any malicious app that asks you to login via another site, like Google or Facebook, can automatically get access to sensitive information,” emphasises the Professor.
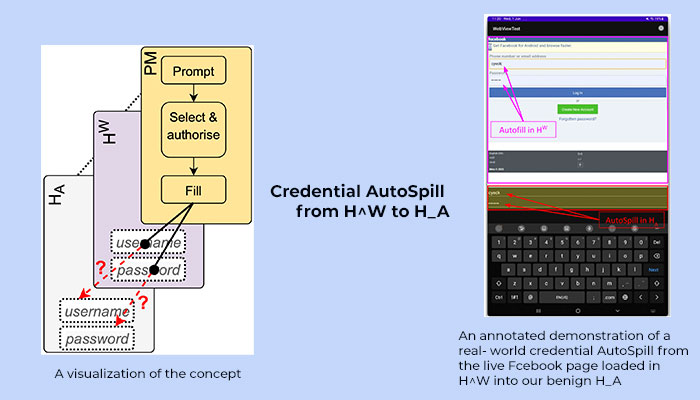
Real World Experiments
What’s interesting is that when the team tested their AutoSpill attack in the real world by using some of the PMs (ranked amongst the top-10 on the PlayStore) on three types of devices with recent Android versions, majority of the PMs were vulnerable to credential leakage even with JavaScript injection disabled. But when JavaScript injection was enabled, all the PMs in the experiment were susceptible to their AutoSpill attack.
Whose Fault Is It Anyway
In order to investigate the why behind the AutoSpill attack, the researchers dug deep into data processing and information exchange between a PM and an android system. Since both Android and PM handle an autofill request with slightly different objectives (security, usability, etc.), they eventually become incompatible from the perspective of the amount of information flowing from one to another. These findings led the team to conclude that both the Android System and the PMs are equally responsible for the credential AutoSpill. “We brought this to the notice of Google as well as the password managers, who then have acknowledged the security breach,” notes the professor, adding that it’s a problem that requires a close-knit coordination between both the PM as well as the OS.
Current Work
The researchers are currently exploring the possibility of a reverse AutoSpill attack. It refers to a scenario where one can extract important credentials from the hosting app to the hosted webpage. “If you are autofilling into a social media app on your phone, there could be a malicious webpage hidden in the background (e.g., an advertisement banner) extracting your sensitive information towards itself,” elaborates Prof. Gangwal. Findings from experiments on such scenarios will be presented as a briefing at the upcoming BlackHat Europe 2023 conference in December. As per the website, BlackHat briefings were created to provide IT professionals a place to learn the latest in information security risks, research, and trends. “It’ll be my first BlackHat talk and I hope to learn new things whilst there, which I can bring back to our campus,” signs off Prof. Gangwal.

Sarita Chebbi is a compulsive early riser. Devourer of all news. Kettlebell enthusiast. Nit-picker of the written word especially when it’s not her own.

Next post